Understanding GRE tunnels using Linux network namespaces
In this blog, lets explore how GRE tunnels work using linux network namespaces.
Introduction
GRE (Generic Routing Encapsulation) is a tunneling protocol that encapsulates a wide varitey of layer-3 network protocols such as IPv4/v6, IPSec e.t.c inside a IPV4 protocol using a virutal point-to-point connection. Due to this reason, GRE tunneling can allow transmission of non-IP protocol traffic over an IP network.
You can think of encapsulation like a courier service. You place your data inside a box and add a to and fro address to it. You leave it to the service provider to take care of the transportation. The transport can involve multipe hops and different modes of transport such as land, air and water. Finally, at the destination, you open the box, take out your data and use it.
GRE Packet structure
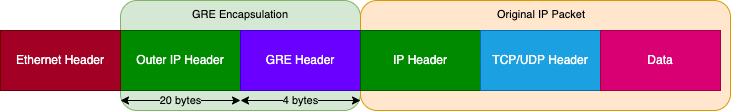
The below picture shows the GRE encapsulation in action. GRE adds two headers to each Layer 3 packet:
- GRE header : This is 4 bytes long and has the protocol type, version and a few other optional parameters.
- Outer IP header : This is 20 bytes long and has the local and remote end points of the GRE tunnel ip address.
Advantages and Disadvantages of GRE tunnels
Benefits and Usecases of GRE tunnels
- Versatile as it can work with a wide variety of L3 protocols.
- Can transport multicast traffic (in contrast to IP-in-IP tunneling)
- Connect IPV6 networks over an IPV4 underlay.
- GRE + IPSEC to create VPNs
- Join two network islands using secure point-to-point links
Disadvantages of GRE tunnels
- Does not support encryption. IPSEC needs to be used in conjunction to close this gap.
- Overhead : an overhead of 24 bytes is added to each network packet. Can lead to fragementation and latency.
MTU on the tunnel interface has been adjusted to 1500 - 24 = 1476 bytes.
5: tun0@NONE: <POINTOPOINT,NOARP,UP,LOWER_UP> mtu 1476 qdisc noqueue state UNKNOWN group default qlen 1000
link/gre 172.16.10.2 peer 152.16.10.2
inet 192.168.50.1/30 scope global tun0
GRE tunnels using network namespaces.
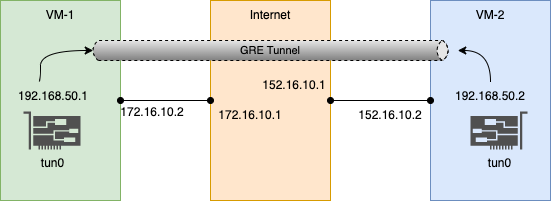
Lets tryout creating GRE tunnels using linux network namespaces. The below pictures shows the topology:
Here, we have 3 network namespaces:
- host1 : ip 172.16.10.2 (veth0)
- internet (router) : ips 172.16.10.1 (veth1), 152.16.10.1 (veth2) (simulates the connectivity via internet routers)
- host2 : ip 152.16.10.2 (veth3)
The hosts are connected to the internet router via veth pairs. IP Forwarding is enabled on the internet router.
Two GRE tunnel end points are created on host1 and host2:
- host1-tun0 : 192.168.50.1/30
- host2-tun0 : 192.168.50.2/30
Setup Script
Here a virtual point-to-point link is formed between host1:192.168.50.1 <—–> host2:192.168.50.2.
Now we can log in to one of our host namespaces and ping the other side of the tunnel.
# ping -c 3 192.168.50.2
PING 192.168.50.2 (192.168.50.2) 56(84) bytes of data.
64 bytes from 192.168.50.2: icmp_seq=1 ttl=64 time=0.094 ms
64 bytes from 192.168.50.2: icmp_seq=2 ttl=64 time=0.112 ms
64 bytes from 192.168.50.2: icmp_seq=3 ttl=64 time=0.124 ms
--- 192.168.50.2 ping statistics ---
3 packets transmitted, 3 received, 0% packet loss, time 2054ms
rtt min/avg/max/mdev = 0.094/0.110/0.124/0.012 ms
A tcpdump capture on the host shows the following packet structure for outgoing icmp request:
08:18:53.986738 IP (tos 0x0, ttl 255, id 18951, offset 0, flags [DF], proto GRE (47), length 108)
172.16.10.2 > 152.16.10.2: GREv0, Flags [none], length 88
IP (tos 0x0, ttl 64, id 16117, offset 0, flags [DF], proto ICMP (1), length 84)
192.168.50.1 > 192.168.50.2: ICMP echo request, id 43241, seq 1, length 64
We can glean the following info from this:
GRE Encapsualtion (Outer IP Header + GRE header):
- IP : IP protocol is being used.
- ttl 255 : maximum ttl value. Indicates the packet is starting from the source.
- flags [DF] : Dont Fragment. Tells the router not to fragment this packet.
- proto GRE (47) : protocol type is 47 for GRE
- length 108 : total size of the packet.
- 172.16.10.2 > 152.16.10.2 : Src ip »> destination ip for packet traversal
- GREv0 : GRE version
Encapsulated IP Packet
Within the GRE tunnel, there’s another IP packet encapsulated:
- IP : IP protocol is being used.
- ttl 64 : ttl value
- proto ICMP (1) : ICMP protocol is being used.
- 192.168.50.1 > 192.168.50.2 : src and destination ips of the point-to-point tunnel link.